Just like a silent spy network, your website is tracking every user's movements in minute detail. Every move they make, including the time and location they made it from, is tracked and recorded by your web servers.
Although you were no doubt already aware of the undercover tracking network that exists on the backend of your web platform, have you done your due diligence on the front end?
Log data, also known as anonymous data or automatic data, must be listed in your Privacy Policy in order to comply with both privacy laws and consumer expectations.
- 1. What is Log Data?
- 2. How is Log Data Used?
- 2.1. Marketing & Analysis
- 2.2. Security Monitoring
- 2.3. Improving System Performance
- 3. Log Data as Personal Information
- 4. Privacy Regulations and Log Data
- 5. Log Data in a Privacy Policy
- 5.1. Which Log Data is Collected
- 5.2. How Log Data Is Used
- 5.3. Third-Party Sharing of Log Data
What is Log Data?

Log data is the information recorded by your web server about when, how, and which visitors are using your website. Web server providers like Apache and NGINX commonly collect the following information about each visitor:
- IP address and device identifier: This is the unique identifying address broadcasted by the browser or device by which each user is accessing your online platform.
- Request date/time: The specific date and time of each action the user takes.
- Page requested: Each page or interface that the user accesses and how long they spend on each page.
- Bytes served: How much information is transferred during the user's activity.
- User agent: Commonly, the web browser or operating system of the user which transfers necessary information to the web server in order to serve the needs of the user.
- Referrer: The previous location that the user was at before they were referred to your website or app, such as a search engine or exterior website link.
- Error logs: Information regarding any errors or functionality problems experienced by the user.
Once the log data has been collected, it will be organized by type so that the web server knows how to use the information. Log data may be organized according to its potential usefulness in categorical logs such as error logs, access logs, and server logs.
How is Log Data Used?

Log data can be incredibly useful for a wide variety of applications, both for programmers or administrators and for marketing analysis. Below are the ways that log data is commonly used.
Marketing & Analysis
For marketing purposes, log data is invaluable. Marketers delve into this information to analyze how visitors find their website, use their website, make purchases, and more.
Here are some strategies for analyzing log data to use in marketing:
- Using referral data to measure how many visitors you receive in response to online advertising campaigns and search engine marketing.
- Analyzing which products or services attract the most visitors using page request data.
- Deciphering lost sales opportunities and potential areas of improvement.
- Examining error data to analyze and improve the user friendliness of your website and sales interface.
- Learning more about customer base with device, browser, and geolocation data, and marketing to incoming customers according to their location.
- Determining which days, months, and seasons the website receives the most traffic.
- Using page request data and time spent on different pages to find out which parts of your site are most successful and attracting/keeping the attention of visitors.
Security Monitoring
Log data works as a forensic trail if ever your website is breached, hacked, or misused in any way.
Here are some ways that log data can be used for security purposes:
- To determine the date, time, and location of a breach
- To ascertain the identity of a hacker or offender
- To identify weaknesses in security and protection measures
- To monitor security and create alert systems in the event of any unauthorized intrusion
Improving System Performance
No code is perfect, and every online business will experience errors and system crashes from time to time. Log data can be crucial in correcting such problems. Here's how:
- Slow response times - Log data can help identify pages or interfaces with slow response times.
- Crash alerts - Website or application crashes due to issues like 'out of memory' or other errors can create alerts so that programmers can respond and resolve them quickly.
- System slowdowns and other software issues - Whenever software problems occur, log data can be used to determine where and how the problems arose.
- General maintenance - By using a log data management or alert system, you can identify any occasion when users encounter an error, recording and reporting the information for improvement purposes.
Although these are not all the possible uses for log files, this list illustrates their necessity in the day-to-day maintenance of a successful online business.
Log Data as Personal Information

First of all, log data is not altogether anonymous, even if it is referred to as such. Some Privacy Policies do name log data as "anonymous" because it does not contain specific personal information like name or email address. However, most privacy lawmakers define personal information as any information that describes an identified or identifiable living individual, including contact information and information that, if combined with other data, can lead to the identification of a particular person.
In other words, even if information does not identify an individual outright, if it can be combined with other data to identify someone, then it must be considered and protected as personal information.
IP addresses, geolocation data, and other log data could potentially be combined with other information like username or online activity to identify a particular person. Therefore, log data can be considered personal information. For this reason, it must be treated as personal information under applicable law.
European documents reflect a similar view of log data. In the next section, we'll go over what this means in regards to privacy laws.
Privacy Regulations and Log Data

Within the past several years, most major privacy enforcement agencies have adjusted privacy regulations to include stipulations regarding log data.
Here are a few pertinent examples that will likely affect your business:
General Data Protection Regulation (GDPR) - The GDPR specifically names device identifiers and geolocation data as personal information, and so the following stipulations will apply to any business that collects log data from EU-based users:
- Disclose all personal information you collect, how and why it's collected, and if it's shared with third parties.
- Notify EU users about their rights in regards to their personal data.
- State your legal basis for collecting personal information and comply with that legal basis.
- Disclose information about how you handle international data transfers, if applicable.
Children's Online Privacy Protection Act (COPPA) - COPPA is designed to protect the personal information (including log data) of children. Depending on whether or not your business is targeted to children, you will either need to:
- Include a statement in your Privacy Policy specifying that your services are not intended for children, or
- Comply with strict parental consent protocols before collecting any log data from children under the age of 13
California Online Privacy Protection Act (CalOPPA) - CalOPPA requires the following conditions to be met for anyone collecting personal data from California residents:
- Disclose the types of information you collect and who you share the information with.
- Provide an accessible method for users to review and edit their personal information.
- Notify users when the Privacy Policy is updated or changed.
- Post an effective date in the Privacy Policy.
- Disclose how your business responds to Do Not Track signals from web browsers.
Although these are not the only regulations and laws that apply to companies who do business on the internet, compliance with the statutes named above will generally cover other less specific regulations regarding privacy.
Log Data in a Privacy Policy

In general, you will need to include three major categories in your Privacy Policy about the log data you collect from users:
- Which log data you collect
- How you use log data
- Who you share log data with
Below we've included some examples of how these categories can be written.
Which Log Data is Collected
Although it goes by different names - anonymous data, automatically collected data, log data - all law-abiding Privacy Policies include a section that describes the types of log data they collect. This section should list out the different types of log data you collect in simple, easy-to-understand language.
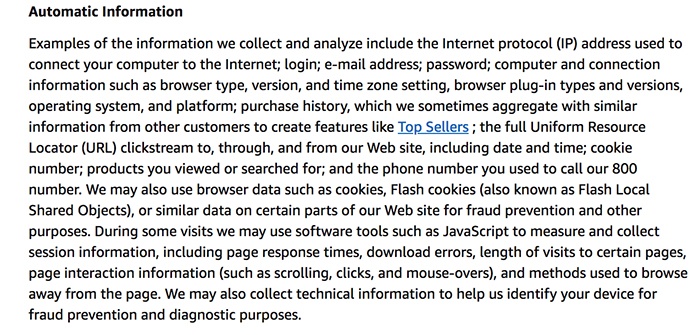
Amazon goes into great detail, listing each log data category and touching on the reasons why each is collected. Listed within this paragraph you will see IP address, browser and operating systems information, geolocation, time stamp, and error reporting data, among others:
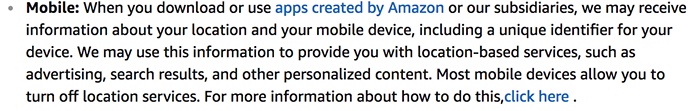
In addition to this, Amazon also includes a paragraph describing the log data collected by its mobile apps:
LinkedIn provides a good example of how to break the list down into shorter, more digestible sections of information:
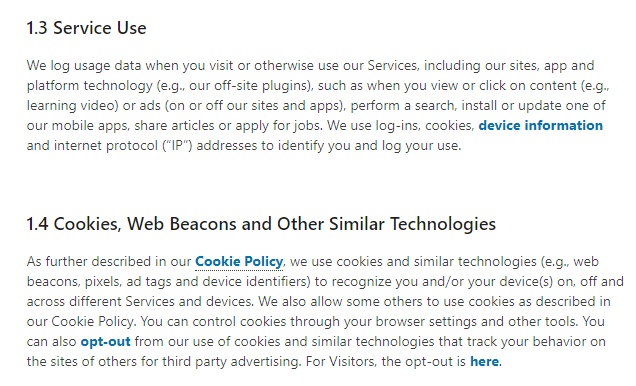
In this example, LinkedIn breaks the information down into smaller paragraphs but still includes information collected about user activity, device and geolocation, as well as information collected via cookies.
How Log Data Is Used
Besides listing out the types of information you collect, it is essential to also list the ways you intend to use log data.
In this section, you must be thorough in order to avoid any potential misunderstandings with users.
It's common for online Privacy Policies to group all data usage information into one long list, which is permissible as long as you include the details of how you use log data.
Here's one such list from the staff management software provider Asana:
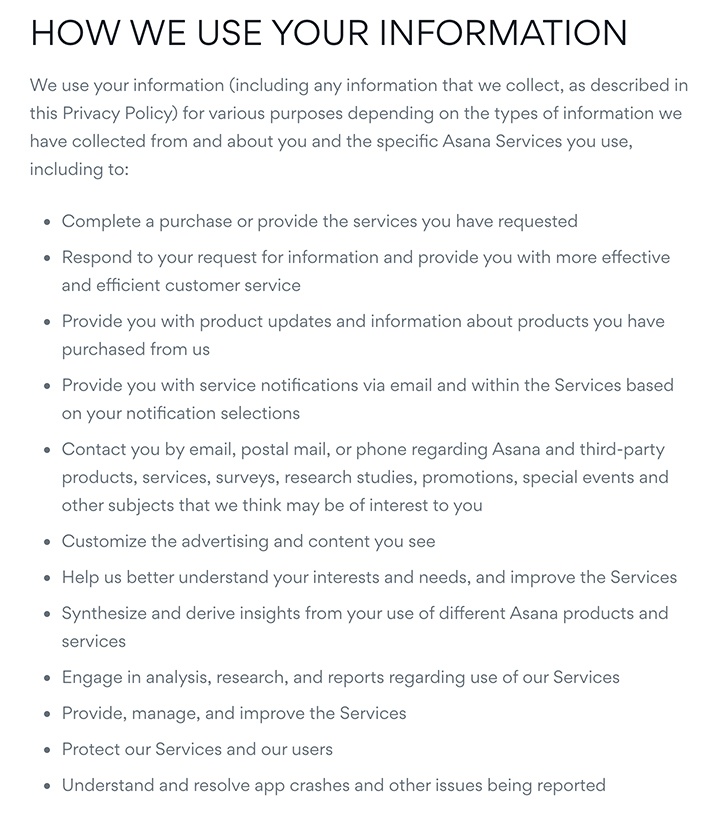
Starting at the bullet point that says "Customize the advertising and content you see," Asana lists the ways in which they use log data. Although it is not specified that this is log data, it is enough that each usage is listed within the Privacy Policy.
Some companies do choose to make the distinction between log data and other personal information, as Apple illustrates here:
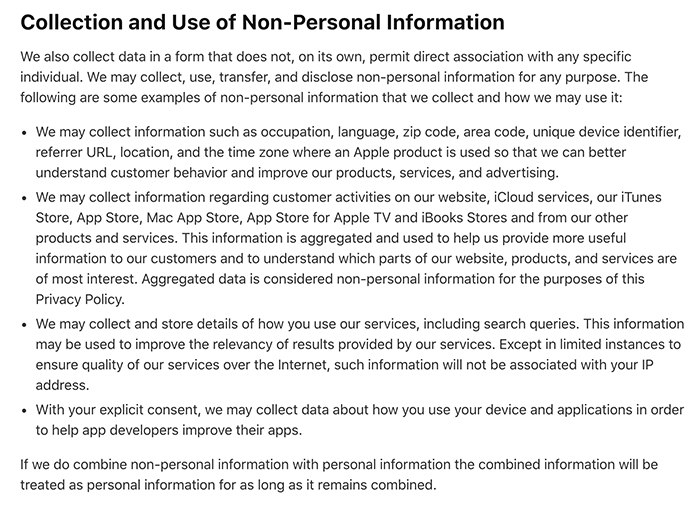
Referring to this as "Non-Personal" information, Apple describes the many ways they use log data for analytical and system-performance purposes. Even though Apple does not consider this data as "personal," they recognize the importance of including each and every usage of log data within the Privacy Policy.
Third-Party Sharing of Log Data
Most major online companies, especially retail and SaaS platforms, outsource marketing analytics to third-party providers in order to better plan online advertising campaigns. This type of analytics requires that the company share customer log data with the third-party providers in order to receive accurate results.
Another reason to share log data with a third party may be for outsourcing programming or administrative work.
Regardless of the reason, it is vital that any third-party sharing is disclosed in the Privacy Policy.
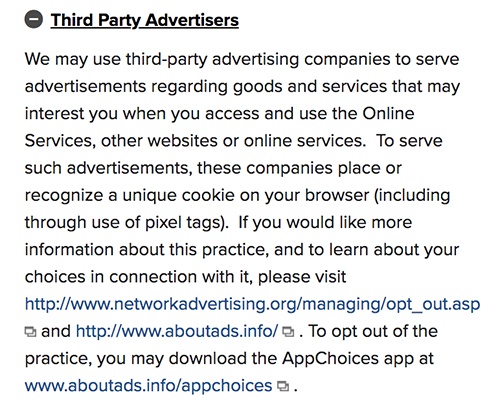
Marriott covers its third-party sharing of log data like so:

The Privacy notice goes on to describe the use of third-party advertisers, which collect log data via cookies:
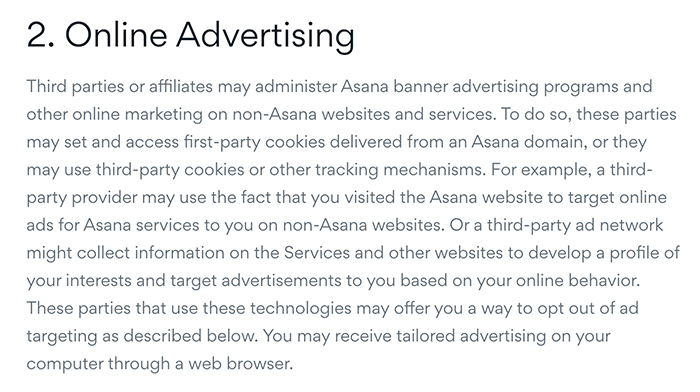
Asana also combines its third-party sharing practices into one paragraph. Although this method is very concise, this section covers all possible reasons for sharing log data in a few quick sentences:

The Policy also mentions log data collected via cookies in the advertising section:
Using your website as an analytical spy can have great benefits, but as you can see, major online companies are very thorough and precise in listing the log data they collect, as well as how it is used and shared.
By following these examples, you can avoid any legal issues as well as potential privacy disputes with your users in the future.

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.